Multi-Level Intrusion Detection and Log Management Systems (ML-IDLMS) in Cloud Computing; A position Paper

Abstract
Cloud computing is a model that provides on-demand access to a shared pool of configurable computing resources over the internet. Cloud computing enables users to scale up or down their resource usage according to their needs and pay only for what they use. Cloud computing also offers benefits such as cost reduction, flexibility, efficiency, and innovation. However, cloud computing also poses significant security challenges, such as data breaches, denial-of-service attacks, unauthorized access, malware infections, and insider threats. Therefore, it is essential to have effective and efficient intrusion detection and log management systems in the cloud computing environment. This paper presents the position that a multi-level intrusion detection and log management system (ML-IDLMS) is a promising solution that can enhance the security and performance of cloud computing by providing a comprehensive and holistic view of the security situation, balancing the trade-off between resource consumption and security service, improving the detection accuracy and reducing the false alarm rate, and empowering the cloud users to participate in the security process. This paper also discusses the current status, future direction, and strengths and limitations of ML-IDLMS.
Introduction & definitions
According to (Shawish and Salama 2013), Cloud computing is a model that provides on-demand access to a shared pool of configurable computing resources (such as servers, storage, networks, applications, and services) over the internet. Cloud computing enables users to scale up or down their resource usage according to their needs and pay only for what they use. Cloud computing also offers benefits such as cost reduction, flexibility, efficiency, and innovation. However, (Alouffi, Hasnain et al. 2021) elaborates that cloud computing also poses significant security challenges, such as data breaches, denial-of-service attacks, unauthorized access, malware infections, and insider threats. Therefore, it is essential to have effective and efficient intrusion detection and log management systems in the cloud computing environment. Intrusion detection is the process of monitoring and analysing the events occurring in a computer system or network to identify possible incidents, which are violations or imminent threats of violations of computer security policies, acceptable use of policies or standard security practices (Sandhu, Haider et al. 2011). Intrusion detection systems (IDSs) are software or hardware tools that perform intrusion detection and alert the system administrators or security personnel of any suspicious events. As defined by (Kent and Souppaya 2006), Log Management is the process of dealing with large volumes of computer-generated log messages, also known as audit records, event-logs generated by various applications, devices, and systems in an IT environment which involves activities such as generating, transmitting, storing, analysing, and disposing of log data. Log management is the process of collecting, storing, analysing, and reporting on the log data. Therefore, Log management systems (LMSs) are software or hardware tools that perform log management and provide useful insights into the system performance, security, and compliance.
Various studies have found out that existing intrusion detection and log management systems in cloud computing environment have some limitations such as (Lee, Park et al. 2011) found out that existing intrusion systems use more resources than necessary while preventing threats, hence having reduced resources left to allocate to users; use the same intrusion detection system for all levels of services available on the cloud environment, which may not be suitable for different types of attacks and scenarios (Chen, Xian et al. 2020); provide platforms for users to monitor their activity logs, but with limited control over submission of suspected threats (Lee, Park et al. 2011); Existing intrusion systems face challenges such as variability, invisibility, and unpredictability of network intrusions in the cloud environment, which makes network intrusion detection increasingly difficult (Chen, Xian et al. 2020); existing intrusion systems have a trade-off between the security level of the IDS and the system performance, which may affect the quality of service and user satisfaction (Lee, Park et al. 2011);
To address these limitations, various research studies including (Lee, Park et al. 2011) (Lala and I.E 2017) have proposed a multi-level intrusion detection and log management system (ML-IDLMS). Therefore, this paper presents a position that ML-IDLMS is a promising solution that can enhance both the security and performance of cloud computing. Also, the status, future direction, challenges, and limitations of ML-IDLMS are discussed.
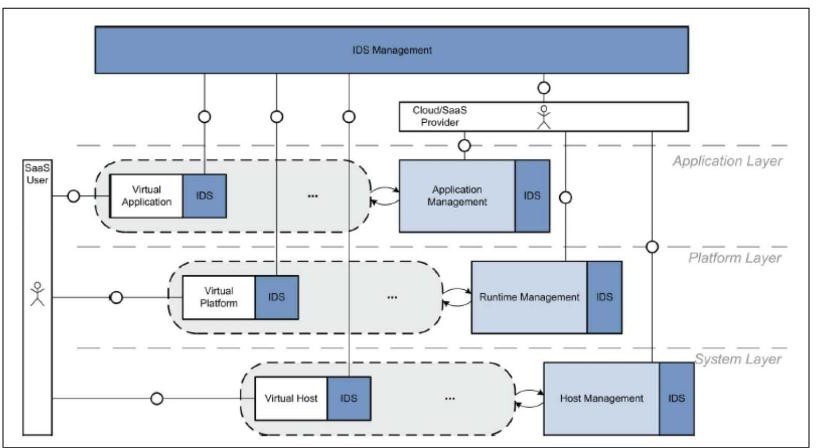
The current status of ML-IDLMS
Literature reveals that ML-IDLMS is still in its conceptual stage and has not been fully implemented in real IT systems and networks but rather an active and promising research area in cloud computing and security. However, several models and methods have been proposed, experimented and evaluated for different scenarios and objectives such as :- (Lee, Park et al. 2011) proposes a method that enables cloud computing system to achieve both effectiveness of using the system resource and strength of the security service without trade-off between them with a method that consists of a multi-level intrusion detection system (ML-IDS) that operates at three levels of granularity: traffic flow level, packet header level, and payload level, uses a fusion decision algorithm (FDA) that fuses the detection results from the MLIDS and the log analysis results from the LMS, and makes a final decision on whether there is an intrusion or not; (Youssif, Kumar et al. 2008) implements a ML-IDS that uses autonomic computing to automate the control and management of ML-IDS with self-adaptive techniques to adjust the parameters or components of ML-IDS according to the feedback from the environment or the users and also uses self-healing techniques to recover from any failures or errors that may occur in ML-IDS; Additionally, leveraging the datasets, such as KDD Cup 99, NSL-KDD, and UNSW-NB15 (Attou, Guezzaz et al. 2023) designed a ML-IDS based on machine learning techniques and (Park, Lee et al. 2023) AI based for detecting intrusions at different levels of granularity in cloud computing environment, and also designed a log management system (LMS) for collecting, storing, analysing, reporting, and visualizing the log data generated by the cloud applications, devices, and systems.
These examples show that multi-level intrusion detection and log management systems are not only feasible but also beneficial for enhancing the security and performance of various cloud systems. However, the same studies mention that there are still many challenges and open issues that need to be solved before it can be widely adopted. Some of these challenges are handling large volumes of network traffic and log data in a distributed manner, achieve high detection accuracy while minimizing resource consumption, balancing the trade-off between resource consumption and security service, ensuring privacy and confidentiality of network traffic and log data, and coping with dynamic and evolving threats that can evade or bypass ML-IDLMS.
How ML-IDLMS Works
The ML-IDS is an IDS that operates at three levels of granularity: traffic flow level, packet header level, and payload level. The traffic flow level IDS monitors the network traffic flows between the cloud users and the cloud servers and detects any abnormal or malicious patterns based on statistical analysis. The packet header level IDS inspects the packet headers of the network traffic, and detects any anomalies or attacks based on signature matching or rule-based analysis. The payload level IDS analyses the payload content of the network traffic, and detects any intrusions or malware based on deep packet inspection or anomaly detection techniques. The ML-IDS assigns different weights to each level of IDS according to their resource consumption and detection accuracy and sends the detection results to the FDA.
The LMS is a system that collects, stores, analyses, and reports on the log data generated by the cloud applications, devices, and systems. The LMS provides a centralized platform for the cloud users and administrators to monitor their activity logs, identify any errors or faults, troubleshoot any problems, audit any compliance issues, and optimize any performance issues. The LMS also enables the cloud users to blacklist any suspected threat IP addresses based on their log analysis. The LMS sends the log analysis results to the FDA.
The FDA is an algorithm that fuses the detection results from the ML-IDS and the log analysis results from the LMS and makes a final decision on whether there is an intrusion or not. The FDA uses a weighted voting scheme to combine the results from different sources based on their reliability and confidence levels. The FDA also considers the feedback from the cloud users based on their blacklisting actions. The FDA then alerts the cloud administrators or security personnel of any confirmed intrusions or attacks.
The future projection of ML-IDLMS
ML-IDLMS is a promising technology that can enhance the security and performance of IT systems and networks by providing a multi-level approach that integrates different sources of information at different levels of granularity, assigns different weights to different levels of IDS according to their performance, uses a fusion decision algorithm that considers multiple factors, and allows the users to monitor their logs and blacklist any suspected threats. However, with the current rapid advancement of technology and artificial intelligence, there is a higher likelihood of solutions to its challenges and limitations which will extend, improve, and incorporate new features and functionalities that can cope with dynamic and evolving threats hence adaptation in real IT system and networks.
Strengths of ML-IDLMS
- It can provide a comprehensive and holistic view of the security situation by integrating different sources of information at different levels of granularity. This can help to detect and prevent various types of attacks, such as network-based, host-based, or application-based attacks, that may target different layers or components of an IT system or network (Yao, Fu et al. 2018).
- As explained by (Park, Lee et al. 2023), It can balance the trade-off between resource consumption and security service by assigning different weights to different levels of IDS according to their performance. This can help to optimize the resource usage and allocation, and to improve the system efficiency and scalability.
- Additionally, ML-IDLMS can improve the detection accuracy and reduce the false alarm rate by using a fusion decision algorithm that considers multiple factors, such as reliability, confidence, feedback, and context. This can help to enhance the system effectiveness and robustness, and to avoid unnecessary or incorrect actions.
- It can empower the users to participate in the security process by allowing them to monitor their logs and blacklist any suspected threats. (Sandhu, Haider et al. 2011) notes that it can help to increase the user awareness and involvement, and to improve the system responsiveness and adaptability.
Weaknesses of ML-IDLMS
- It may require high computational and communication overheads to collect, store, analyse, and fuse large amounts of network traffic and log data from different sources and levels. This may affect the system performance and availability and may introduce new vulnerabilities or risks (Yao, Fu et al. 2018).
- According to (Kumar 1995, Yao, Fu et al. 2018), It may face difficulties in handling heterogeneous, incomplete, inconsistent, or noisy data from different sources and levels. This may affect the system quality and reliability and may lead to errors or conflicts.
- It may be vulnerable to attacks that target its components or communication channels, such as spoofing, tampering, replaying, or denial-of-service attacks. This may affect the system integrity and confidentiality and may compromise its functionality or security.
- (Alouffi, Hasnain et al. 2021) mentions that ML-IDLMS may raise ethical or legal issues regarding the privacy and confidentiality of network traffic and log data that are collected and analyzed by ML-IDLMS. This may affect the user trust and satisfaction and may violate some regulations or policies.
In conclusion, ML-IDLMS is a promising technology that can enhance the security and performance of IT systems networks by providing a multi-level approach that integrates different sources of information at different levels of granularity, assigns different weights to different levels of IDS according to their performance, uses a fusion decision algorithm that considers multiple factors, and allows the users to monitor their logs and blacklist any suspected threats. However, ML-IDLMS still has some challenges and limitations that need to be addressed before it can be widely adopted. ML-IDLMS can also be extended and improved by incorporating new features and functionalities and the use of artificial intelligence that can cope with dynamic and evolving threats
References
- Alouffi, B., M. Hasnain, A. Alharbi, W. Alosaimi, H. Alyami and M. Ayaz (2021). "A Systematic Literature Review on Cloud Computing Security: Threats and Mitigation Strategies." IEEE Access 9: 57792-57807.
- Attou, H., A. Guezzaz, S. Benkirane, M. Azrour and Y. Farhaoui (2023). "Cloud-Based Intrusion Detection Approach Using Machine Learning Techniques." Big Data Mining and Analytics 6(3): 311-320.
- Chen, L., M. Xian, J. Liu and H. Wang (2020). Intrusion Detection System in Cloud Computing Environment. 2020 International Conference on Computer Communication and Network Security (CCNS).
- Kent, K. A. and M. Souppaya (2006). "Guide to Computer Security Log Management."
- Kumar, S. (1995). Classification and detection of computer intrusions, Purdue University.
- Lala, O. and O. I.E (2017). MULTI-LEVEL INTRUSION DETECTION AND PREVENTION WITH LOG MANAGEMENT SYSTEM IN A CLOUD COMPUTING ENVIRONMENT.
- Lee, J.-H., M.-W. Park, J.-H. Eom and T.-M. Chung (2011). Multi-level intrusion detection system and log management in cloud computing. 13th International Conference on Advanced Communication Technology (ICACT2011), IEEE.
- Lee, J. H., M. W. Park, J. H. Eom and T. M. Chung (2011). Multi-level Intrusion Detection System and log management in Cloud Computing. 13th International Conference on Advanced Communication Technology (ICACT2011).
- Park, C., J. Lee, Y. Kim, J. G. Park, H. Kim and D. Hong (2023). "An Enhanced AI-Based Network Intrusion Detection System Using Generative Adversarial Networks." IEEE Internet of Things Journal 10(3): 2330-2345.
- Sandhu, U. A., S. Haider, S. Naseer and O. U. Ateeb (2011). A survey of intrusion detection & prevention techniques. 2011 International Conference on Information Communication and Management, IPCSIT.
- Shawish, A. and M. Salama (2013). Cloud computing: paradigms and technologies. Inter-cooperative collective intelligence: Techniques and applications, Springer: 39-67.
- Yao, H., D. Fu, P. Zhang, M. Li and Y. Liu (2018). "MSML: A novel multilevel semi-supervised machine learning framework for intrusion detection system." IEEE Internet of Things Journal 6(2): 1949-1959.
- Youssif, A.-N., A. Kumar, S. Hariri, G. Qu, Y. Luo and F. Szidarovsky (2008). "Multi-Level Intrusion Detection System (ML-IDS)." International Conference on Autonomic Computing.